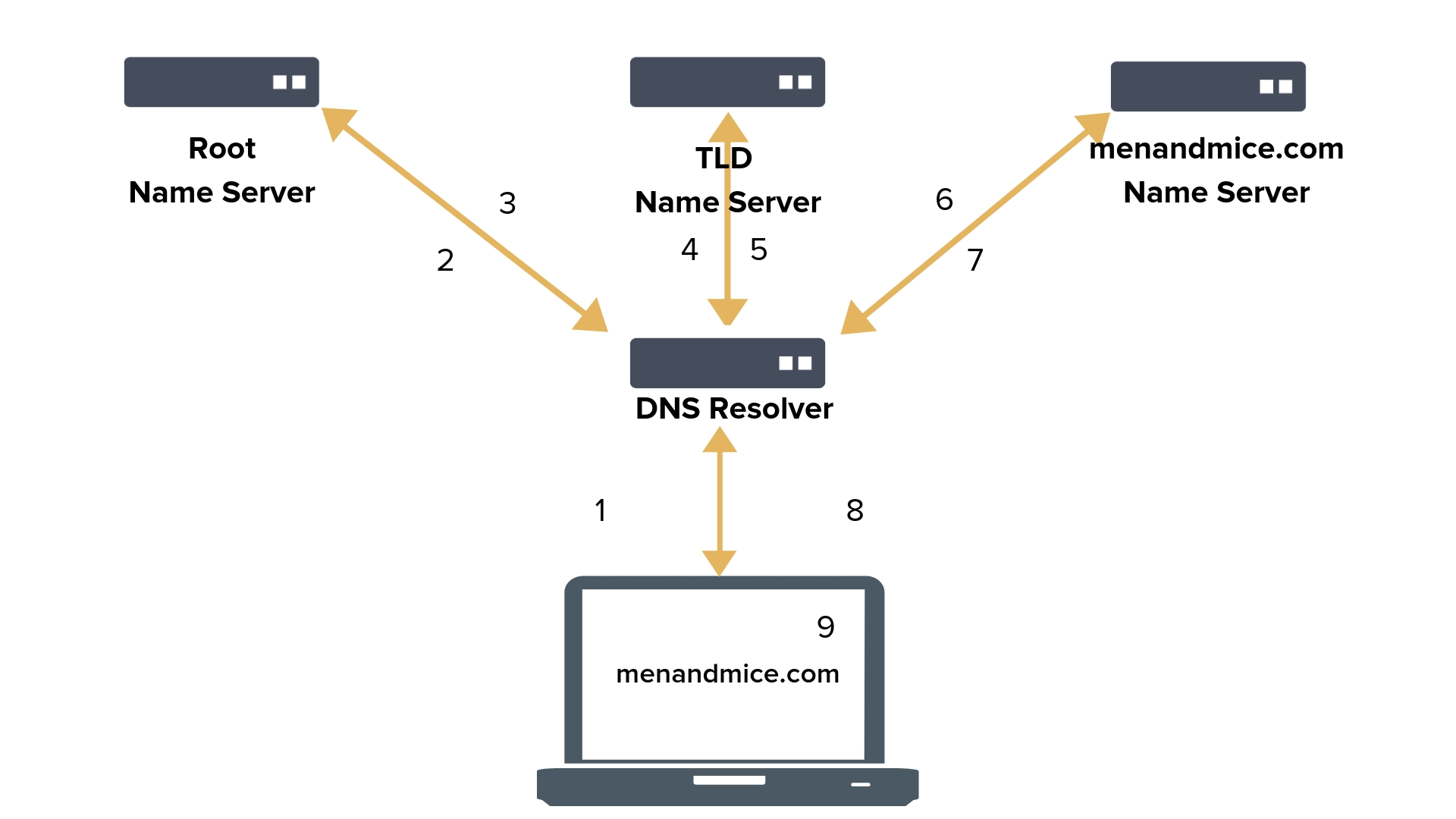
DNS is plain-text UDP with no assurance of authenticity or integrity of the data.
Flaws:
- Privacy of data collected on the name servers, any query sent to the resolver is necessarily visible to the resolver.
- Any data exchanged between the client and the resolver is transmitted unencrypted and unauthenticated.
- Integrity and authenticity, any data exchanged can be manipulated in transit.
DNSSEC (DNS Security Extensions)
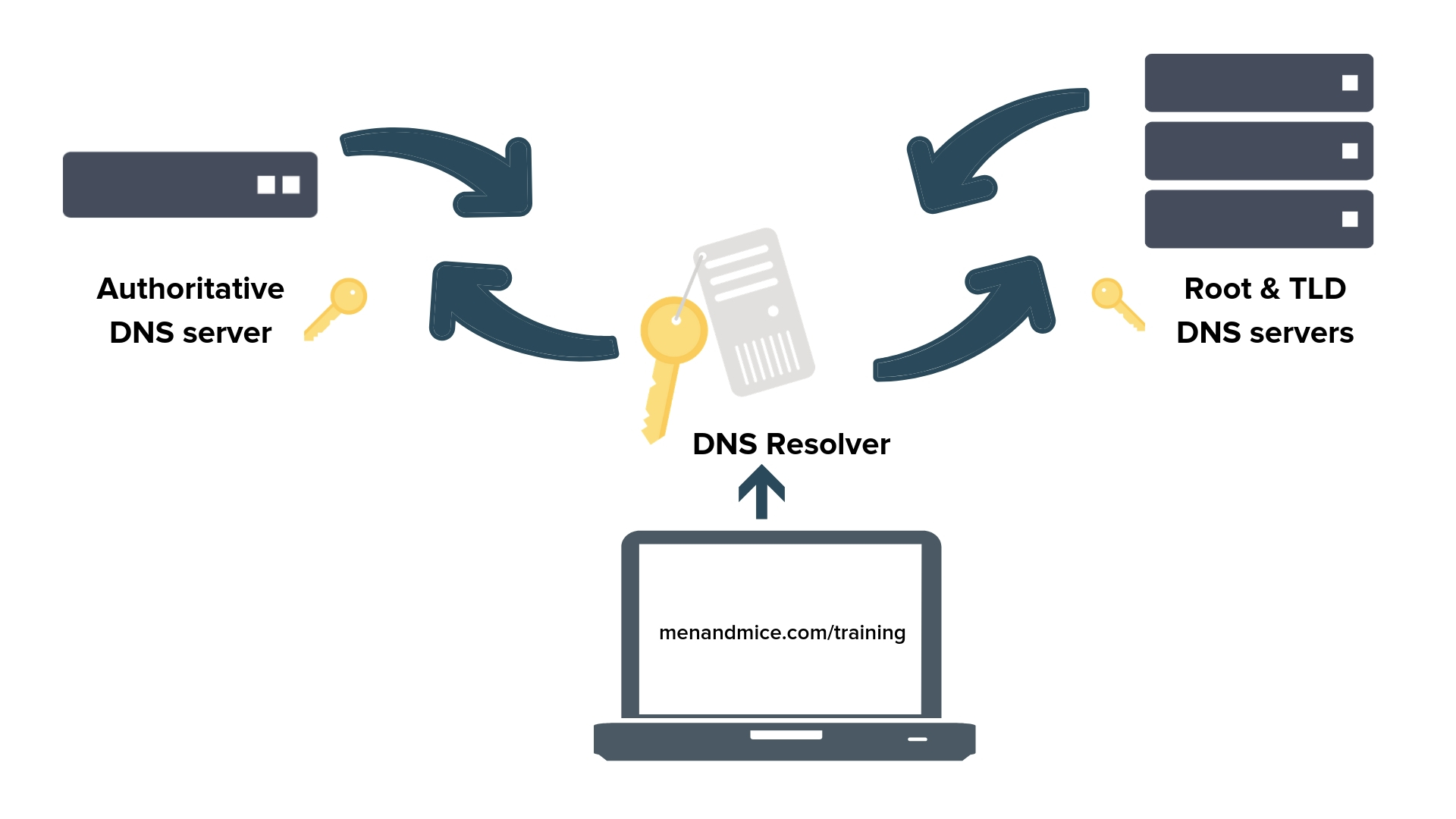
DNSSEC creates a secure DNS by adding cryptographic signatures to existing DNS records.
These digital signatures are stored in DNS name servers alongside common record types like A, AAAA, MX, CNAME, etc.
They verify that a requested DNS record comes from its authoritative name server and wasn’t altered en-route.
Every DNS zone has a public/private key (zone-signing key pair - ZSK). Any recursive resolver that looks up data in the zone, also retrieves the zone's public key which is used to validate the authenticity of the data.
It also secure threats to DNS including stealing DNS admin credentials and changing zone files,Denial of Service (DoS) attacks,DNS spoofing but the communication is still sent in cleartext.
DoT (DNS Over TLS)
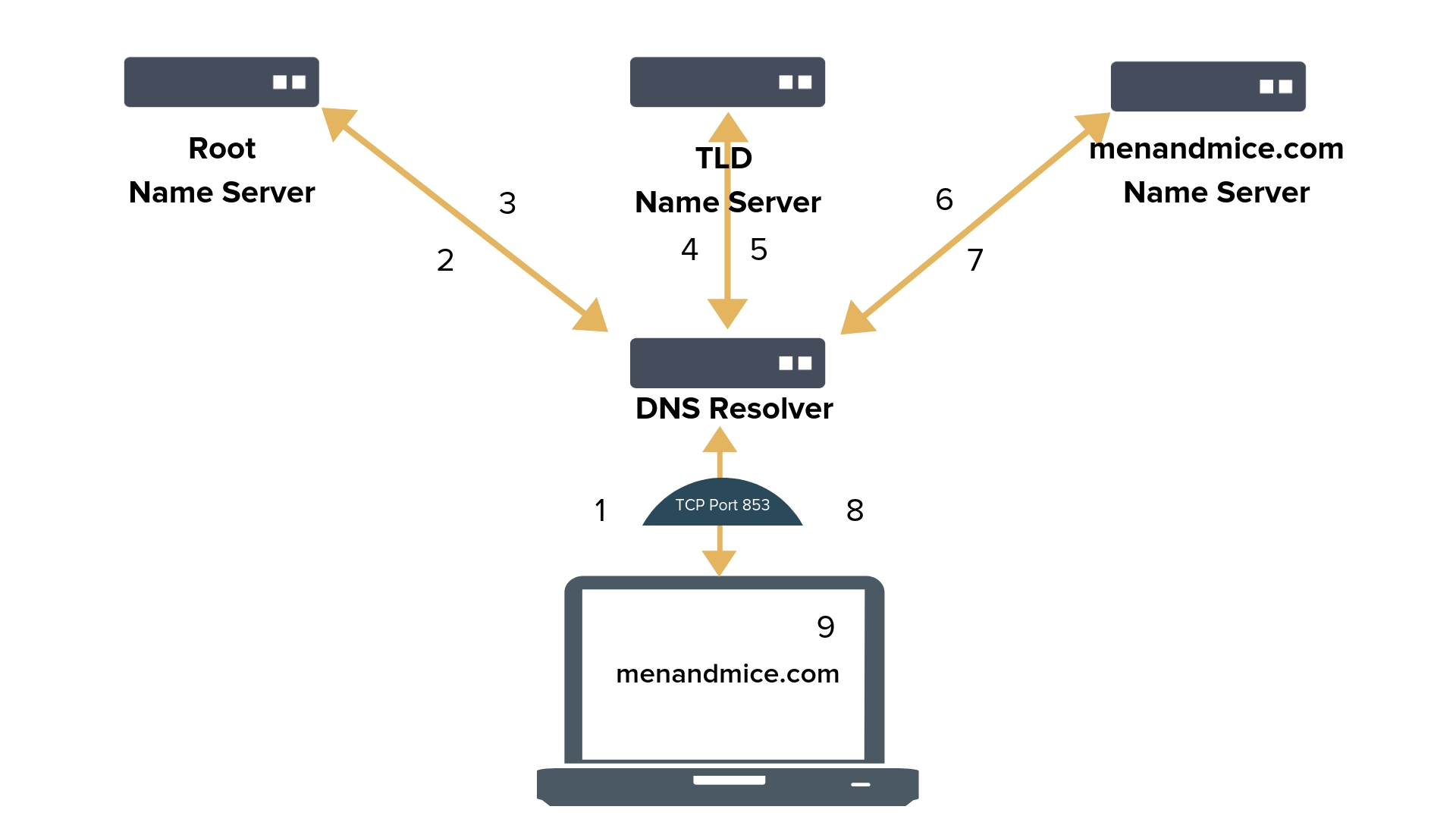
It wraps DNS queries and answers (DNS traffic) via the Transport Layer Security (TLS) protocol.
It uses TCP port 853.
Weakness: It only addresses encryption on a system resolver level and works only on one port. Target the traffic between the resolver and the nameservers or block the port and DoT is over.
DoH (DNS Over HTTPS)
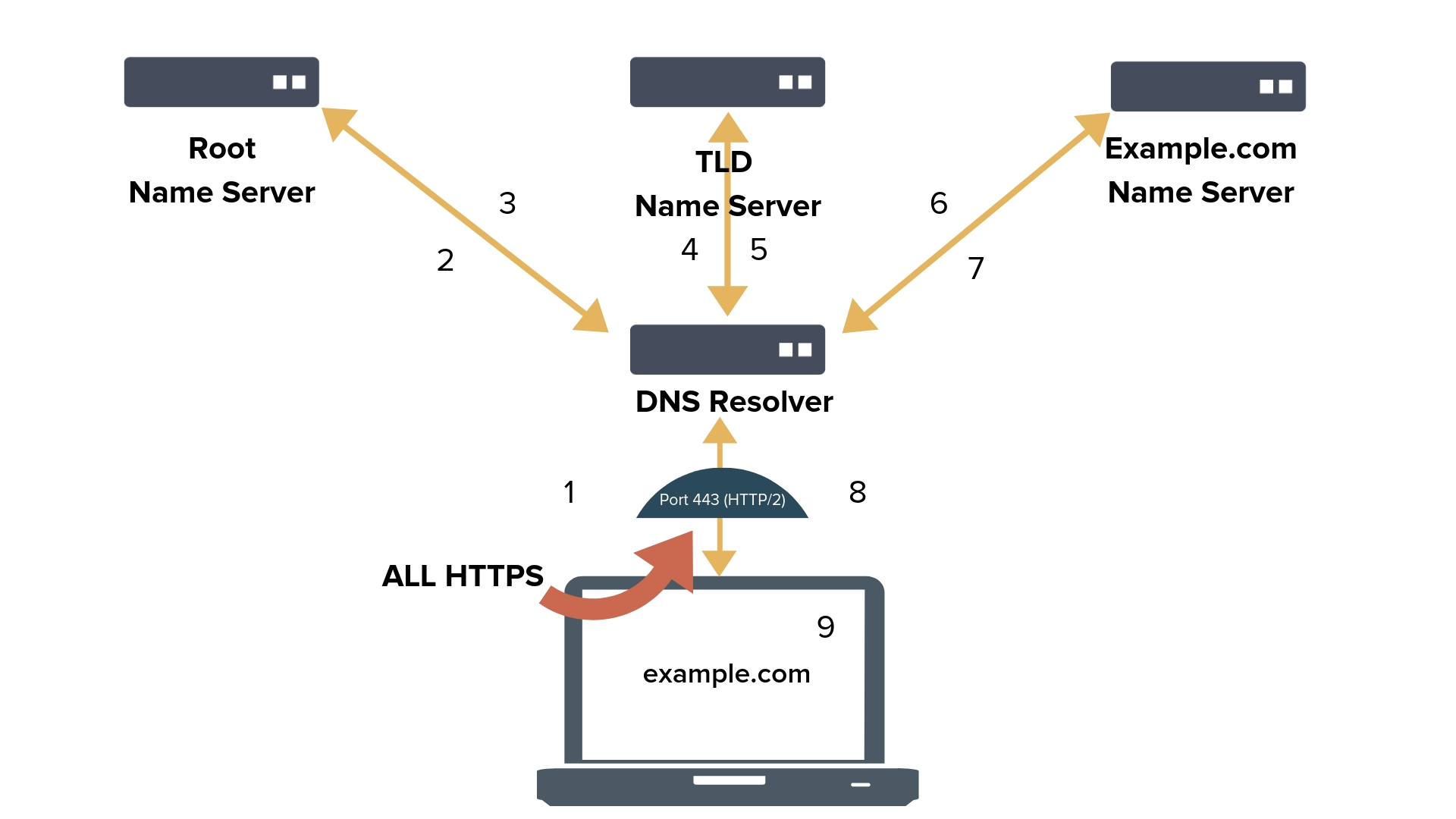
In it DNS traffic is mixed in with regular HTTPS traffic. HTTPS uses TLS to.
DoH was specifically designed as a solution for web applications (i.e., browsers)